In today’s fast –moving tech world, most projects rely on multiple packages and libraries. These packages often release new versions with improvements, bug fixes, and most importantly security patches. If we are not keeping up with these updates, project might be exposed to vulnerabilities that hackers can exploit. Manually checking each package for the latest version and updating can be a time-consuming and repetitive task. To simplify and automate this process, there’s a tool called Dependabot. This document provides a clear and friendly overview of why Dependabot is important and how we can integrate it into our project.
About Dependabot.
Dependabot is a handy tool developed by GitHub that helps keep your project dependencies up to date. It automatically scans your repository’s dependency files (such as package.json, requirements.txt, or package-lock.json), checks for newer or more secure versions of the libraries you use, and creates pull requests to update them.
It takes care of the following:
- Notifying you about vulnerabilities in packages.
- Automatically fixing those vulnerabilities.
- Keeping all dependencies current with minimal effort from developer side.
Key Features of Dependabot
- Dependabot Alerts: Lets you know when a dependency in project has a known security issue.
- Dependabot Security Updates: Automatically open pull requests to fix vulnerable packages.
- Dependabot Version Updates: Regularly checks for new package versions and creates PRs to update them.
Why do we need Dependabot in repository.
When project depends on many packages, each with their own updates and security fixes, keeping up can become overwhelming. Without automation this leads to:
- Time-consuming.
- Error-prone.
- Increases risk of security vulnerabilities.
Dependabot solves all this by automating the process and making sure project stays safe and up to date without constant manual efforts.
How to enable Dependabot in GitHub Repo.
- Go to the main page of the repository.
- Navigate to the ‘Settings’ tab.
- In the left side bar, go to Security > Advanced Security.
- Uder the Dependabot section, enable:
- Dependabot Alerts.
- Dependabot Security Updates.
- Dependabot Version Updates.
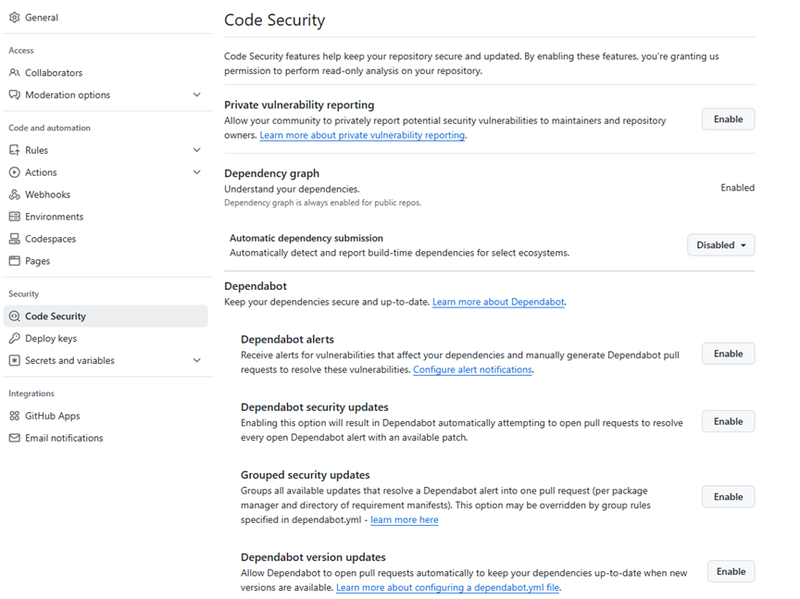
Once version updates are enabled, GitHub will generate a file called dependabot.yml inside .github folder of the repo.
Setting Up dependabot.yml file:
We can configure dependabot.yml file according to the project requirement. But on top level it should consist minimum of:
version: 2
updates:
- package-ecosystem: "npm" # or "pip", "maven", etc.
directory: "/"
schedule:
interval: "weekly"
Beyond these basics, we can also configure:
- Registering private registries.
- Set custom labels for pull requests.
- Assigning reviewers.
- Defining update frequency (daily, weekly, etc..).
Where can we find Dependabot alerts.
- In repository, go to the Security tab.
- From the left sidebar, click Vulnerability Alerts.
- We’ll see a list of alerts triggered by Dependabot.
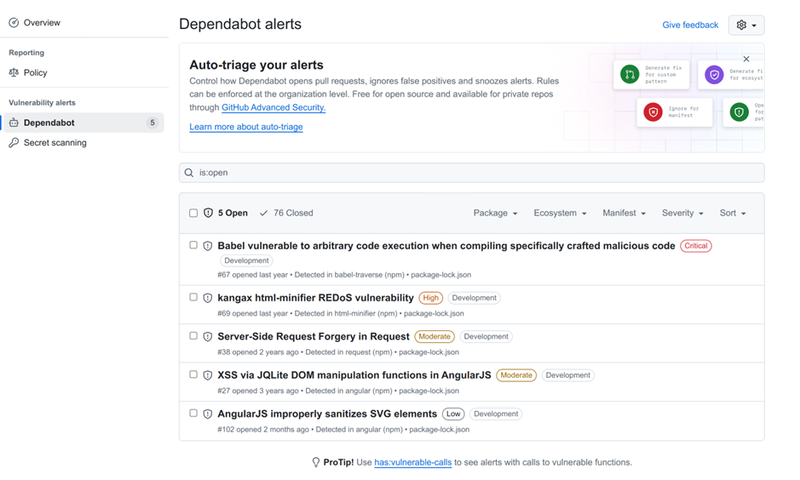
Each alert includes helpful details like:
- Severity level.
- Affected package and version.
- The patched version.
- Description of the issue.
Key Takeaways:
- Keeping dependencies updated is essential for project security and stability.
- Manual updates are time-consuming and error-prone.
- Dependabot automates dependency management by regularly checking for updates, identifying security vulnerabilities, and automatically creating pull requests with the required changes.
- It can be easily enabled in any GitHub repository.
- Configuration is flexible and supports private registries, custom labels, update schedules, and more.
With Dependabot, we can focus on building features and less on chasing dependency updates, while keeping your codebase safe.